MeSign Zero Trust Security Solution IntroductionNever trust, Verify signature, Encrypt all.
1. Introduction to Zero Trust and Zero Trust Security
The concept of "Zero Trust" was proposed in 2010 by John Kindervag, the chief analyst of Forrester Research. The core concept is that all people and things are untrustworthy, any request for resources is subject to trust management and security control. Now, major security vendors have launched their own zero trust security solutions. The NIST also released the SP 800-207 "Zero Trust Architecture" guidance document in August 2020, giving the definition of ZTA and the general deployment model and use cases that zero trust can improve the overall information technology security of the enterprise. With the increasing pressure to protect business systems and data, and attacks become more and more complex, enterprise CIOs, CISOs and other executives are increasingly agreeing to the concept of zero trust and implementing zero trust security solutions, to adapt to the complex network environment, support mobile office and protect users, equipment, applications and data in any location more effectively.
"Zero Trust", in layman's terms, means not trusting anyone or anything. Zero Trust is a security concept, and there is no fixed technology. Its core belief is that organizations should not automatically trust any people and things inside or outside its perimeters and instead must verify anything and everything trying to connect to its systems before granting access. The Zero Trust model fundamentally contained the old ideas of castles and moats, because new technologies such as cloud computing and mobile office have been widely used, and the methods of protecting castle-and-moat are no longer feasible. It should always be assumed that the network is full of threats, external and internal threats fill the network all the time. You cannot rely solely on network locations to establish trust relationships. All devices, users, and network traffic should be authenticated and authorized to access all systems.
However, Zero Trust security solutions currently on the market generally have the following three problems:
- (1) Only emphasize the importance of identity authentication and access control. Complicated dynamic continuous trust evaluation and dynamic adjustment of access permissions are required. This is because we don’t know who the bad guys are, and we can only rely on Holmes’ continuous screening, which is not only too inefficient and easy to make mistakes, but also makes the system very complex and difficult for management.
- (2) Forget what the goal of zero trust security is. The goal of any security solution is to protect data, and Zero Trust security is the same. It is to allow the "right people" to access the "right servers" and obtain the "right data".
- (3) Forget what technology the key technology is to solve the trust problem! What technology can effectively protect data security! Of course, it is PKI (Public Key Infrastructure) technology. PKI technology was born to solve the problem of trust! Born to solve data security issues! PKI technology completely solves (1) data confidentiality (Privacy); (2) data production and user identity authenticity (Authentication); (3) data integrity (Integrity); (4) data generation behavior and use behavior’s non-repudiation, the four headaches (PAIN) data security issues. Typical applications of PKI technology are digital signatures, encryption and time stamping.
MeSign Technology has more than 15 years of experience in PKI technology product research and development and application services, and has built MeSign cloud cryptographic infrastructure, enabling the client software-MeSign App to realize automatic email encryption and automatic document digital signatures. And MeSign Technology opens up cloud cryptographic infrastructure, provides cloud cryptographic services, turns cryptographic capabilities into a resource service of cloud computing, empowers all client software and Internet applications, so that all software developers and Internet service providers do not need to repeat investment to build cryptographic infrastructure, just purchase cryptographic services on demand based on business needs, and quickly use cryptographic capabilities to help businesses operate securely and reliably.
Based on this, MeSign Technology puts forward its own Zero Trust security solutions based on PKI technology and cloud cryptographic services according to users’ requirements for Zero Trust architecture. The difference from the Zero Trust security solutions of traditional network security vendors, they still focus on protection, but out solution is to directly protect the data, the goal of being protected. We believe that PKI technology is the most effective and efficient reliable technology to solve trust problems and protect data security. According to the definition of cryptography, it refers to technologies, products and services that use specific transformation methods to encrypt and protect information. The use of cryptographic technology to achieve user authentication and information encryption protection can solve the problems that Zero Trust wants to solve, and at the same time, it can also meet users' compliance requirements of the related laws and regulations.
2. Introduction to MeSign Zero Trust Security Solution Learn more about MeSign Zero Trust Security Solution
2.1 Four basic principles
First, MeSign Zero Trust security solution is not to replace the existing network security solutions and discard the existing network security protection equipment and systems, but to plan and implement Zero Trust security solution based on the existing network security protection equipment and protection systems and transform existing security protection systems to gradually support zero trust security. Zero Trust security is not the goal but protecting data assets and ensuring data security are the goals. Zero Trust security is not only suitable for Internet security, but also for Internet of Things security, Internet of Vehicles security, and Industrial Internet security. The Zero Trust architecture will eventually become the industry standard configuration, which means that every organization is on the Zero Trust journey, and network security has actually been developing towards the direction of Zero Trust security!
Second, there is no standard process for building a Zero Trust security system. Organizations need to choose appropriate technical solutions and construction solutions based on their own business security needs. The construction of a Zero Trust security system cannot be accomplished overnight. The organization needs to make a deployment plan based on the existing security infrastructure and implement it gradually after a certain technical measure has been fully tested. The construction of a Zero Trust security system requires the participation and cooperation of all departments, and a top-down project management mechanism needs to be established to promote the smooth implementation of this project.
Third, the fundamental task of zero trust security is to protect data from being illegally obtained, and do not trust anyone or anything, no matter where they are! The future development direction of network security is to completely solve the trust problem, not to improve the protection ability. The network is secure because of trust! The task of network security is to protect data, which is secured by encryption.
Fourth, MeSign Zero Trust security solution fully adopts PKI technology to achieve strong identity authentication, digital signature, encryption and time stamping. We do not trust identities without digital signatures, data without digital signatures, and data without encryption, do not trust the time without a timestamping, and do not trust the location information without a location stamping.
MeSign Zero Trust security solution can be summarized in three phases: Never trust, Verify signature, Encrypt all. That is to say, only trust identities with digital signatures (persons/things/data), digital identities must be presented and verified for each access to the required resources, all data are encrypted with certificates, and all data should be time stamped.
2.2 Solution introduction
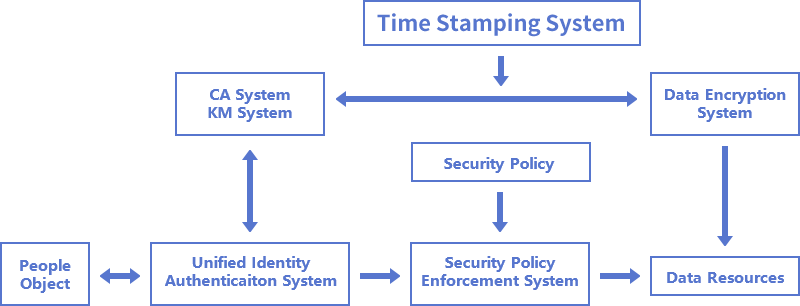
MeSign Zero Trust security solution is based on PKI technology, relying on the established MeSign cloud cryptographic infrastructure and the already provided MeSign cloud cryptographic service, to provide users with reliable Zero Trust security, which not only solves the trust problem, but the most important thing is to solve the data security issues, use digital signatures and encryption to protect data security. As shown in the figure below, MeSign Zero Trust security solution mainly consists of three parts: Unified identity authentication system, Security policy enforcement system, and Cryptographic service system. The cryptographic service system is mainly composed of a CA system, a key management (KM) system, and time stamping system and data encryption service system (including digital signature service).
Whether it is people or things (including terminal equipment, network equipment, servers, objects, industrial equipment, vehicles, etc.), each subject must have two digital certificates (signing certificate and encrypting certificate), which are issued by the CA system and the KM system to prove their digital identity and for data encryption. This is the core of MeSign Zero Trust security solution, and it is also different from other Zero Trust security solutions at present. Our solution is that each person and thing must pass identity validation to obtain a trusted digital identity, rather than anonymously untrustworthy. Identity makes the subsequent identity authentication system and security policy enforcement system very simple and makes trust management simpler.
Each subject has a digital identity, and people and things can be divided into different levels of identities according to business needs and signing certificates with different validation levels can be issued. This is the same as using different certifications in different application scenarios in the real world. If a person or thing needs to access data resources, it needs to present a corresponding signing certificate to prove its identity. The identity authentication system verifies the user's digital signature to identify whether its identity is trusted. If it is not trusted, it will be rejected directly. If it is trusted, the security policy enforcement system determines whether the user can access the requested resource. Organizations must formulate different security policies according to business needs. For example, users with different identity validation levels can access different data resources. After a security policy is formulated, the security policy enforcement system can control which resources users can access. Of course, the premise is that the user can pass the trusted identity authentication.
The third important system is the Data encryption service system. Many Zero Trust security solutions do not have this component. We think this component is very important, because the goal of any security solution is to protect data, and Zero Trust security is the same. The data encryption service system is composed of a digital signature system, an encryption system, and a time stamping system. It provides digital signature services for data to prove the identity of the owner of the data and the identity of the producer of the data and provides encryption services for the data. The data will loss the stolen value only be ciphered, this makes the security protection system simpler. It also provides a time stamping service for the data to prove the data production time, which is very important for application scenarios that require post-audit and verification.
Simply put, MeSign Zero Trust security solution is an identity authentication and data encryption solution based on PKI technology, which is similar to real-name air travel in the real world. It ensures the safety of air travel through real-name authentication of passengers and airline qualification certification. The current Zero Trust solutions on the market require complex dynamic continuous trust evaluation and dynamic adjustment of access permissions. This is because non-real-name authentication does not know who the bad guy is, and can only rely on Sherlock Holmes's continuous screening, which is too inefficient, and It is easy to make mistakes in judgment.
3. Analysis of the advantages of MeSign Zero Trust security solutions
MeSign Zero Trust security solution has four major features: more advanced technology, simpler architecture, easier to use, and data more secure. It can meet the user’s application requirements for Zero Trust security deployment and ensure that users can deploy Zero Trust architecture based on the existing network security architecture. It only needs to make appropriate transformations to effectively adapt to the increasingly complex network environment, support mobile office and protect users, equipment, applications and data at any location.
(1) More advanced technology
Zero Trust is to solve the trust problem, and the trust service is the CA certificate service, and the PKI technology is the only reliable technology to solve the trust problem. And in addition to network security protection technology, the most secure protection is encryption. The purpose of security is to protect data,when data is encrypted, it is secure, then it loses the value of being attacked. This is the ultimate security. An important application of PKI technology is to encrypt data with certificate. Therefore, MeSign Zero Trust security solution adopts PKI technology and uses cryptography to completely solve the trust and security issues. This solution is more advanced and at the same time satisfies the user's compliance requirements of the related laws and regulations.
(2) The data is more secure
This is the biggest highlight of MeSign Zero Trust security solution. The true meaning of security is to protect data. Therefore, encrypt every data that needs to be protected to realize the whole process of ciphertext transmission and ciphertext storage. Only in this way can the data be truly protected and secure. For example, email security, after the email is written, it is automatically encrypted with a certificate, which not only realizes the end-to-end encryption security protection of email confidential information, but also saves it in cipher text in the email server to ensure the "lifetime" security of the confidential information in the email.
(3) Simpler architecture
MeSign Zero Trust security solution uses digital certificates to achieve strong identity authentication, which is not only secure than the username/password method, but also simpler. There is no need to do more continuous dynamic trust evaluations, making the Zero Trust architecture simpler. Easier to implement and lower implementation cost.
(4) Easier to use
MeSign Zero Trust security solution adopts digital certificate to realize strong identity authentication, users do not need to memorize various usernames and passwords of various systems, which is not only more secure, but also easier to use. For security policy administrators, it is also easier to set security rules that only need to present different certificates according to the type of business. This is consistent with the real-world security inspection rules. For example, an ID card or passport is required for boarding, a driver's license is required for driving a vehicle, and so on.