MeSign Zero Trust Security SolutionNever trust, Verify signature, Encrypt all.
1. Preliminary understanding of MeSign Zero Trust Security Solution
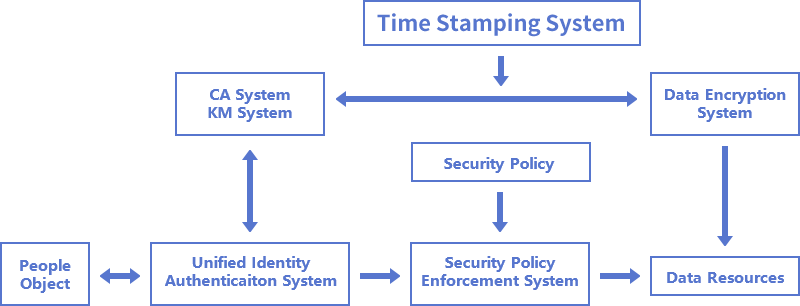
MeSign Zero Trust security solution is based on PKI technology, relying on the established MeSign cloud cryptographic infrastructure and the already provided MeSign cloud cryptographic service, to provide users with reliable Zero Trust security, which not only solves the trust problem, but the most important thing is to solve the data security issues, use digital signatures and encryption to protect data security. As shown in the figure below, MeSign Zero Trust security solution mainly consists of three parts: Unified identity authentication system, Security policy enforcement system, and Cryptographic service system. The cryptographic service system is mainly composed of a CA system, a key management (KM) system, and time stamping system and data encryption service system (including digital signature service).
Whether it is people or things (including terminal equipment, network equipment, servers, objects, industrial equipment, vehicles, etc.), each subject must have two digital certificates (signing certificate and encrypting certificate), which are issued by the CA system and the KM system to prove their digital identity and for data encryption. This is the core of MeSign Zero Trust security solution, and it is also different from other Zero Trust security solutions at present. Our solution is that each person and thing must pass identity validation to obtain a trusted digital identity, rather than anonymously untrustworthy. Identity makes the subsequent identity authentication system and security policy enforcement system very simple and makes trust management simpler.
Each subject has a digital identity, and people and things can be divided into different levels of identities according to business needs and signing certificates with different validation levels can be issued. This is the same as using different certifications in different application scenarios in the real world. If a person or thing needs to access data resources, it needs to present a corresponding signing certificate to prove its identity. The identity authentication system verifies the user's digital signature to identify whether its identity is trusted. If it is not trusted, it will be rejected directly. If it is trusted, the security policy enforcement system determines whether the user can access the requested resource. Organizations must formulate different security policies according to business needs. For example, users with different identity validation levels can access different data resources. After a security policy is formulated, the security policy enforcement system can control which resources users can access. Of course, the premise is that the user can pass the trusted identity authentication.
The third important system is the Data encryption service system. Many Zero Trust security solutions do not have this component. We think this component is very important, because the goal of any security solution is to protect data, and Zero Trust security is the same. The data encryption service system is composed of a digital signature system, an encryption system, and a time stamping system. It provides digital signature services for data to prove the identity of the owner of the data and the identity of the producer of the data and provides encryption services for the data. The data will loss the stolen value only be ciphered, this makes the security protection system simpler. It also provides a time stamping service for the data to prove the data production time, which is very important for application scenarios that require post-audit and verification.
Simply put, MeSign Zero Trust security solution is an identity authentication and data encryption solution based on PKI technology, which is similar to real-name air travel in the real world. It ensures the safety of air travel through real-name authentication of passengers and airline qualification certification. The current Zero Trust solutions on the market require complex dynamic continuous trust evaluation and dynamic adjustment of access permissions. This is because non-real-name authentication does not know who the bad guy is, and can only rely on Sherlock Holmes's continuous screening, which is too inefficient, and It is easy to make mistakes in judgment.
2. Zero Trust security solution based on MeSign cloud cryptographic service
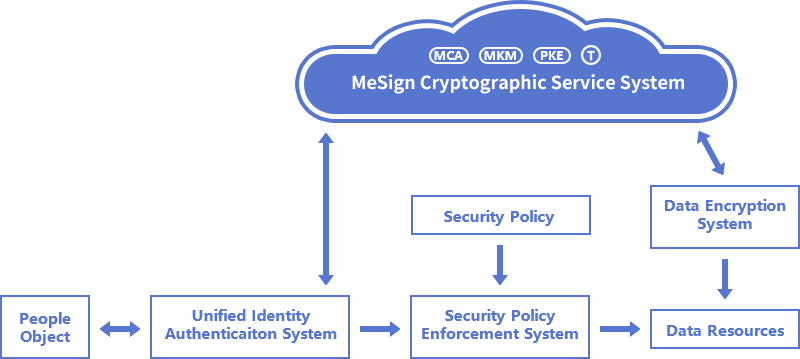
MeSign Zero Trust security solution is based on PKI technology, but users do not need to invest in the construction of the corresponding PKI/CA system and rely on the MeSign cloud cryptographic service to provide users with the cryptographic services required for Zero Trust security. This has the advantage of not only saving PKI system investment, reducing the cost of system operation and maintenance, but also can quickly deploy a Zero Trust architecture to quickly achieve Zero Trust security. As shown in the figure below, MeSign Zero Trust security solution includes a unified identity authentication system, a security policy enforcement system, and a data encryption service system, together with the MeSign cloud cryptographic service system, to jointly realize a Zero Trust security architecture.
2.1 Unified Identity Authentication System
The unified identity authentication system is a basic system. It is necessary to conduct a comprehensive investigation of all persons and things that can connect to the server resources of the organization to obtain data resources. All persons and things (equipment) must be included in the identity management system and all must be classified according to the classification of people and things, which resources can be accessed by different users to confirm the identity certificate (signing certificate) of which authentication level is required.
For people, MeSign unified identity authentication system supports 5 different security levels of identity types, uniformly using the user's email address as the username, specifically:
- (1) V0 level: username/password weak authentication method, only validates the username and password, do not validate the email control, the lowest security level, can only access some unimportant resources. This insecure authentication level is reserved for compatibility with some old systems that cannot disable the username/password authentication method in a short time;
- (2) V1 level: digital certificate strong identity authentication method, which only validates the user's email control, without user identity information. Users at this level can only access resources that do not require real user identity information, and can only guarantee that they are indeed the users with this email address;
- (3) V2 level: The digital certificate strong identity authentication method, not only validates the user's email control, but also validates the user's personal identity, which is a trusted personal identity. Users at this level can access the system that must be logged in as an individual to obtain data related to their personal identity;
- (4) V3 level: The digital certificate strong identity authentication method, not only validates the enterprise domain email control, but also validates the identity of the organization, which is a trusted organizational identity. Users at this level can log in to the system as an organization to obtain data related to the organizational identity;
- (5) V4 level: The digital certificate strong identity authentication method, not only validates the enterprise domain email control, but also validates the identity of the organization and organization employee identity, which is a trusted identity of organization employee. Users at this level can access the system that must be logged in as an employee of the organization to obtain data related to the identity of the employee.
In other words, a person either a quasi-anonymous identity that only validated the email address or is a real name validated personal identity or an organization employee identity, and each email address can only be bound to one unique identity. Each person may have multiple identity certificates, which are used in different application scenarios to present different certificates. This is the same as real-world identity authentication and it is effective and efficient. It is impossible to have low effectiveness that requires continuous evaluation and continuous screening. If a person or thing needs to access data resources, it needs to present a corresponding signing certificate to prove its identity. The identity authentication system validates the user's digital signature to identify whether its identity is trusted. If it is not trusted, it will be rejected directly. If it is trusted, the security policy enforcement system will then determine whether the user can access the requested resource.
For things, different identity certificates can be issued according to different purposes, different functions or belonging to different organizations, or they can be distinguished according to different access rights. This requires users to combine their own business management system to divide and define the certificate types.
When people and things are connected to the unified identity authentication system for the first time, the authentication system is responsible for completing their identity validation and applying for corresponding digital certificates (including signing certificates and encrypting certificates) from MeSign Cloud Cryptographic Service System. The user keeps the private key locally or in the cloud key management system based on business needs. At the same time, it should also record the IP address and location information at the first access to determine whether the user violates other security principles when accessing the authentication system. For example, it is impossible for a person to use the same signing certificate to access at different locations at the same time to access the authentication system.
The unified identity authentication system also has the function of applying to the CA system for revocation of a certain certificate. Once an identity certificate is found to be illegally used, the identity authentication system cannot be passed, and a certificate revocation application will be initiated in real time to complete the revocation of the certificate in real time. This operation is equivalent to the operation of revoking the lost certification or ID card in the real world.
2.2 Security Policy Enforcement System
The security policy enforcement system is responsible for the formulation, management and execution of security policies. Organizations must formulate different security policies according to business needs. For example, users with different identity levels can access different data resources. After the security policy is formulated, when the user passes the identity authentication, the security policy enforcement system controls which data resources the user can access.
The step of formulating a security strategy is very important. It is necessary to subdivide the statistics of various resources in the organization into the database and formulate different access strategies according to different network segments, different servers, different databases, and different data items. This strategy needs to be formulated for users with different identities. For example, this data can only be viewed by company executives. It is necessary to check the identity certificate information of the visitor who has passed the identity authentication and confirm that it is indeed an executive before allowing access to the required data resources.
In order to confirm the identity of cloud data resources, security policy formulation not only requires users to meet certain identity conditions in order to access data resources, but also should formulate policies that require the resource server to show its own identity certificate when users submit data to the server. Only when the server identity complies with the security policy can the user be allowed to submit data to the server, which ensures that the user will not submit confidential data to a cloud server with a fake identity. Two-way authentication and confirmation of security policies ensure that users can get the data they need and that users submit their data to the correct server.
2.3 Data encryption service system
The data encryption service system includes encryption service, digital signature service and time stamping service. This is the core system of MeSign Zero Trust security solution, and it is also the biggest difference from other solutions. The goal of Zero Trust security is to protect data. Our Zero Trust concept is to distrust identities without digital signatures, distrust data without digital signatures, distrust unencrypted data, distrust no timestamped time, distrust no location stamped location information. The data encryption service system is to make every piece of data have an identity, are encrypted, are timestamped, and are location stamped (according to business needs).
When data is generated, it should use the digital signature of the data producer's identity certificate to classify and identify the data, then accurately establish a secure access strategy. At the same time, it is necessary to ensure the ownership of the data, the production responsibility, and the legally effective time for audit. Data encryption is to make the user data secure in the database. It is encrypted with the public key of the person who has the right to access it, and the person who has the right to access it can obtain the encrypted data after passing the authentication and security policies, then the user can use his private key to decrypt the data. This is to say, this data can only be used by those who have the right to read it, and other people cannot decrypt the data even if they get it. This is true Zero Trust security.
The data encryption service system calls the MeSign cloud cryptographic service according to business needs to realize the digital signature, encryption and time stamping service of the unidentified cleartext data, so that all data have a trusted identity, encrypted, trusted time and trusted location information, thus truly protecting data security.
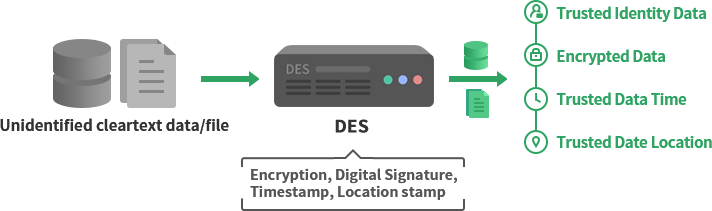
2.4 MeSign Cloud Cryptographic Service System
The digital signature, encryption and time stamping services provided by the data encryption service system are provided by MeSign Cloud Cryptographic Service. Users can choose appropriate services and service packages according to their business needs, including pay-per-use, monthly or annual billing methods. MeSign Zero Trust Security Solution supports SDK or API to call MeSign cloud cryptographic service.
MeSign Cloud Cryptographic Service is that MeSign Technology opens the mature cloud cryptographic infrastructure as a cloud cryptography service to all Internet application developers and Internet service providers, turning cryptographic capabilities into a cloud service for all client software and Internet applications, so that all developers and service providers do not need to repeatedly invest in the construction of cloud cryptographic infrastructure, but purchase cryptographic services on demand according to their own application needs, which not only greatly saves investment, but more importantly, can quickly use cryptography capabilities to help businesses operation securely and reliably. At the same time, it meets the user's compliance requirements for all data and privacy laws and regulations, and protects valuable customer data resources and data assets, thereby greatly enhancing the core competitiveness of the enterprise.
MeSign Cloud Cryptographic Service is an innovated cryptographic capability delivery model, which is a deep integration of cloud computing technology and cryptographic technologies such as identity authentication, data encryption, digital signature, and timestamping. Cryptographic as a Service integrates cryptographic products, cryptographic usage policies, cryptographic service interfaces and service processes in accordance with the requirements of cloud computing technology architecture, and combines cryptographic system design, deployment, operation and maintenance, management, and billing into one service to satisfy users' cryptographic application requirements. Users no longer need to "purchase" cryptographic hardware or cryptographic systems and other cryptographic products, but use the cryptographic functions provided in the cloud cryptographic infrastructure in the form of "rental" cryptographic services. MeSign Cryptography as a Service has ten features such as on-demand service, out-of-the-box, fast integration, flexible expansion, ease of use, lower cost, standardized use, global compliance, stronger applicability, and secure operation and maintenance, which can meet all cryptographic application requirements such as data encryption protection (certificate encryption), trusted data identity (digital signature), trusted data produce and use time (time stamping), and trusted data produce and use location information (location stamping).
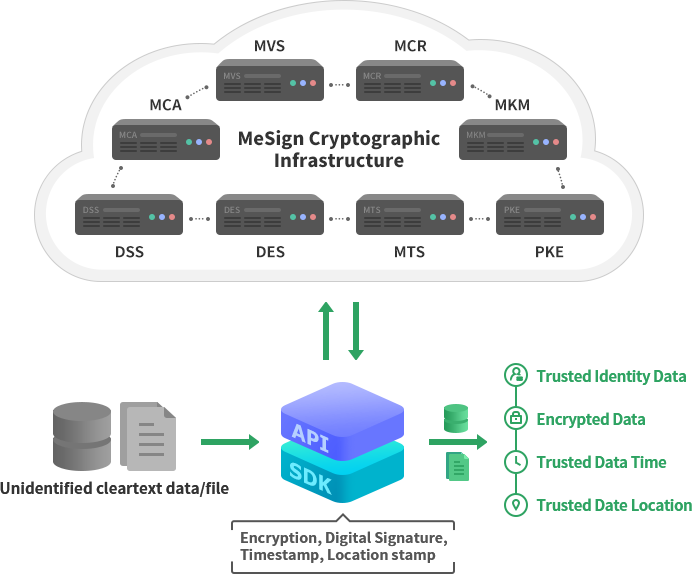
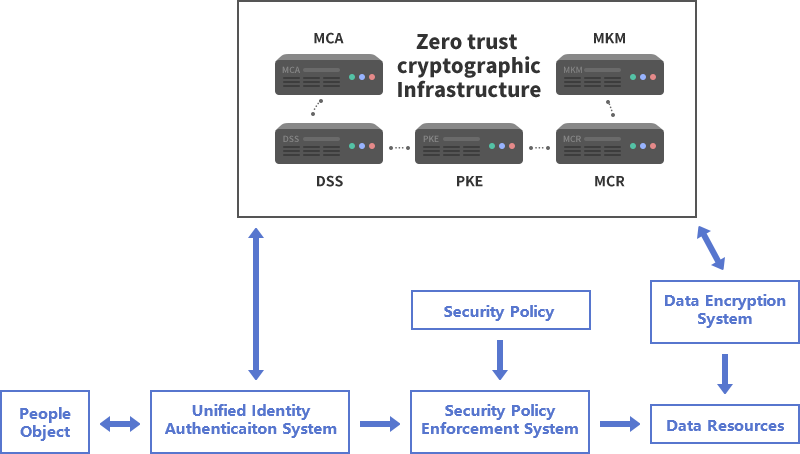
3. Zero Trust security solution based on self-deployment of cryptographic infrastructure
The difference from the above Zero Trust security solutions using cloud cryptographic services is that users build their own Zero Trust cryptographic infrastructure to provide the required cryptographic services for Zero Trust security, as shown in the figure below, which mainly include CA system, Key Management (KM) system, Time Stamping Service system, Certificate Revocation Status system and Public Key Exchange system. It provides all cryptographic services called by the Unified Identity Authentication system and Data Encryption Service system include the issuance of signing certificates and encrypting certificates to users, digital signature services, encryption services, and time stamping services.
The other parts of this scheme are the same as the above scheme. The advantage is that all cryptographic services are autonomous and controllable. The disadvantage is that it increases the system investment, management, and secure operation and maintenance of cryptographic services. It is suitable for government agencies and large enterprises.
4. Summary
MeSign Zero Trust security solution is based on the practical solutions that MeSign Technology has developed for many years on the basis of email security and document security application practices. It does not copy any other party’s solution, but it is an innovative solution based on MeSign Technology’s rich experience in the products development and application of PKI technology. Zero Trust is only a very good security concept and security strategy, and each security company needs to combine its own technical advantages to provide different solutions to solve the Internet trust problem.
PKI technology is the most reliable technology to solve the trust problem, which has also been well tested by MeSign Technology in email security and document security application practices. And users must have the cryptographic capability required by the PKI technology based Zero Trust security solution, can choose MeSign cloud cryptographic service or self-deploy a cryptographic service system to achieve it. It is very flexible and can meet the practical applications of various organizations of different sizes.
MeSign Zero Trust Security Solution not only solves the trust problem, but also solves the data security problem. It is very practical and welcome to contact us.